Видео с ютуба Database Vulnerabilities

Wordfence Intelligence Weekly Vulnerability Report | November 10, 2025 to November 16, 2025
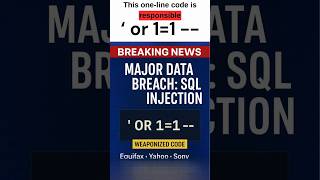
SQL-инъекция: взлом базы данных в одну строку за 60 секунд! 🤯

"Chinese Hackers Can Hack Anything"- But India Still Keeps Database in Paper. #CyberSecurity #shorts

Django Vulnerabilities Expose Apps to SQL Injection & DoS Attacks

24. Docker #Image #Security with #Grype | Scan Docker #Image for #Vulnerabilities & #Container

How Do ORMs Prevent SQL Injection Vulnerabilities?

Tenable Vulnerability Management and Superna Data Attack Surface Management Overview

POV: You deleted a customers database

HOW TO TEST YOUR IoT DEVICES FOR VULNERABILITIES

NoSQL Injection — Joseph Simon Unveils Hidden Vulnerabilities at FOXXCON Meetup November

100,000 WordPress Sites Affected by Privilege Escalation Vulnerability in AI Engine Plugin

MongoDB Insights: изучение уязвимостей и безопасности баз данных в Hack The Box

Massive Data Exposures, Insider Threats, and State-Sponsored Cyber Attacks

Scan WordPress Websites Using WPScan on Linux #linux #hacker #shorts

FederatedCode: Using ActivityPub for Open Data Federation

How to Detect AccessControl Vulnerabilities in Smart Contracts | Glider Demo

Day 99 | National Vulnerability Database #cybersecurity #ethicalhacking #hacker #chatgpt #gemini

Day 90 | Exploit-DB #cybersecurity #ethicalhacking #kali #hacker #ai #chatgpt #aishorts #gemini

How Attackers Exploit SQL Injection (SQLi) + Real Examples

Know About Exploit Database — the researcher’s toolbox for real-world vulnerabilities!